Securing FieldShield Encryption Keys with Alliance Key Manager
In a previous article, we detailed a method for securing the encryption keys (passphrases) used in IRI FieldShield data masking jobs through the Azure Key Vault. Read More

In a previous article, we detailed a method for securing the encryption keys (passphrases) used in IRI FieldShield data masking jobs through the Azure Key Vault. Read More

This is the first of a two-part blog series detailing data class validation in IRI Workbench. This article provides an overview of our provided validation scripts and how to use them in a data discovery or classification job. Read More

IRI Workbench users can connect to and manipulate the data in the underlying database in Salesforce using theJDBC and ODBC drivers from CData or Progress Software. Read More

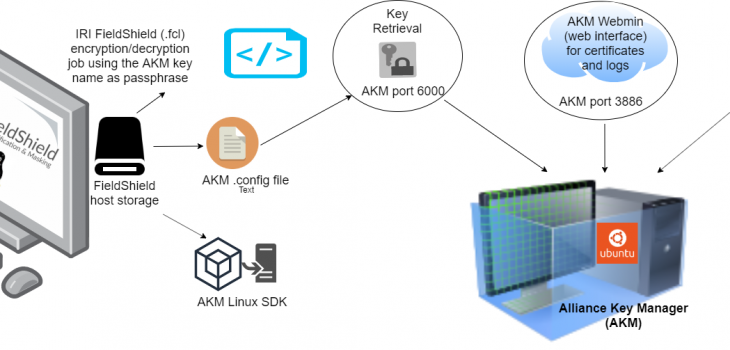
One of the primary uses of IRI FieldShield is to encrypt and decrypt sensitive data in database or flat-file columns. FieldShield relies on a passphrase to derive a symmetrical encryption key used at encryption and decryption time. Read More

The Data Class File Masking Job wizard in IRI Workbench protects large numbers of structured file sources that have been previously classified. While it was possible to use the data classes in many of the existing wizards, if the data class library included a lot of classified fields, selection of the classified sources was cumbersome. Read More

Splunk Phantom is an orchestration, automation, and response technology for running “Playbooks” to respond to various conditions. Phantom connects to Splunk Enterprise using the Phantom App for Splunk, so that actions can be taken on knowledge derived from data indexed in Splunk. Read More

This article demonstrates the use of IRI DarkShield to identify and remediate (mask) personally identifiable information (PII) and other sensitive data in MongoDB, Cassandra, and Elasticsearch databases. Read More

Article 17 of the General Data Protection Regulation (GDPR) stipulates the need to minimize aging data through deletion, as well as the ad hoc Right to Erasure, often referred to as the Right to be Forgotten. Read More

Usually static data masking is performed on production data at rest so it is stored safely, or when replicated to non-production environments for testing or development purposes. Read More

The Splunk Adaptive Response Framework (ARF) included with Splunk Enterprise Security (ES) allows actions to be taken in response to data. This is done by creating an alert that triggers when a certain search result condition is received in the Splunk ES Search and Reporting app. Read More

Production or test data targets, as well as the operational log data, created by SortCL-compatible data manipulation or generation jobs in the IRI Voracity data management platform and its included products (IRI CoSort, NextForm, RowGen, FieldShield and DarkShield) are all machine-readable. Read More